我正在使用 FirewallD 版本 1.1.1 和 Ubuntu 版本 22.04.2 LTS,当我将 IP 添加到受信任区域时,它会被 docker 区域阻止。
知道为什么会发生这种情况吗?以及我该如何解决它。
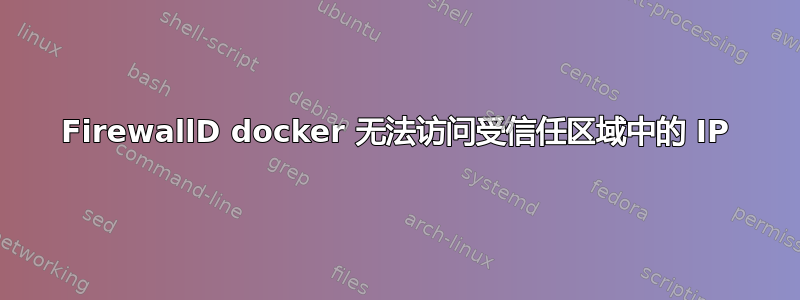
这是我的防火墙配置。
block
target: %%REJECT%%
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
dmz
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
docker (active)
target: ACCEPT
icmp-block-inversion: no
interfaces: br-1d3369241dbf br-2441d78a6847 br-41ed9dc53492 docker0
sources:
services:
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
drop
target: DROP
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
external
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
home
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
internal
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
nm-shared
target: ACCEPT
icmp-block-inversion: no
interfaces:
sources:
services: dhcp dns ssh
ports:
protocols: icmp ipv6-icmp
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule priority="32767" reject
public (active)
target: default
icmp-block-inversion: no
interfaces: enp1s0f0
sources:
services: custom--2406-3546 custom--25565-25567 custom--31195-31195 custom--64306-64306 custom--8123 custom--8803-8804 custom--http-alt dhcpv6-client ssh
ports: 80/tcp 443/tcp 2022/tcp 7552/tcp 7552/udp 31194/udp 31194/tcp 31195/tcp 31195/udp
protocols:
forward: no
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
trusted (active)
target: ACCEPT
icmp-block-inversion: no
interfaces:
sources: <IP1>
services: custom--81
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
work
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
这是输出docker network inspect bridge
[
{
"Name": "bridge",
"Id": "7a4c15265efd8957091d9311bbeb98bd438d71314c7c2e457c8dc551896b9152",
"Created": "2023-05-26T05:41:34.923141769Z",
"Scope": "local",
"Driver": "bridge",
"EnableIPv6": true,
"IPAM": {
"Driver": "default",
"Options": null,
"Config": [
{
"Subnet": "172.17.0.0/16",
"Gateway": "172.17.0.1"
},
{
"Subnet": "fd00:dead:beef:c0::/80",
"Gateway": "fd00:dead:beef:c0::1"
}
]
},
"Internal": false,
"Attachable": false,
"Ingress": false,
"ConfigFrom": {
"Network": ""
},
"ConfigOnly": false,
"Containers": {
"8f1e9b77ca2b2b24a282b717b4fe17cab0d76f8f1279d3e3578a7d01fa303a9b": {
"Name": "watchtower",
"EndpointID": "5c2d2e29231df7af83b5fdadd73372ca3b46f5e4aaf29df1b7e04f2b0aa384c6",
"MacAddress": "02:42:ac:11:00:02",
"IPv4Address": "172.17.0.2/16",
"IPv6Address": "fd00:dead:beef:c0:0:242:ac11:2/80"
}
},
"Options": {
"com.docker.network.bridge.default_bridge": "true",
"com.docker.network.bridge.enable_icc": "true",
"com.docker.network.bridge.enable_ip_masquerade": "false",
"com.docker.network.bridge.host_binding_ipv4": "0.0.0.0",
"com.docker.network.bridge.name": "docker0",
"com.docker.network.driver.mtu": "1500"
},
"Labels": {}
}
]
更新1
到目前为止,我设法让事情正常运转,但我仍然不确定这是否是正确的方法
firewall-cmd --zone=trusted --remove-source=<IP2>
firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 0 -i br-2441d78a6847 -j ACCEPT
firewall-cmd --permanent --direct --add-rule ipv4 filter OUTPUT 0 -o br-2441d78a6847 -j ACCEPT
firewall-cmd --add-rich-rule='rule family=ipv4 source address=<IP2> accept' --permanent
firewall-cmd --zone=trusted --add-rich-rule='rule family=ipv4 source address=<IP2> accept' --permanent


