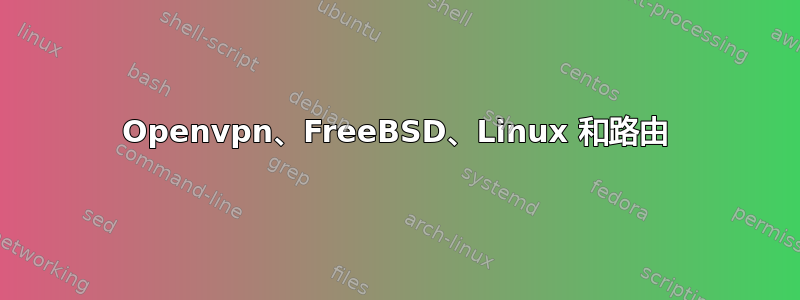
办公室里有一个网络,网络里有一个运行FreeBSD的路由器,外面有一个运行CentOS的服务器。
任务:提供从任何地方访问办公室网络的权限。
数据:网络 — 192.168.0.0,位于 FreeBSD 后面,bge0(192.168.0.111)和 re0(192.168.1.2 — 位于调制解调器的子网中)。外部服务器 — xx.xx.xx.xx。OpenVPN 网络中的 FreeBSD 为 192.168.255.6,CentOS 服务器地址为 192.168.255.1
问题:外部服务器无法访问内部网络(我可以访问 FreeBSD 路由器),但我可以从我的网络访问外部服务器。我需要从外部服务器访问内部网络。
CentOS 服务器的 OpenVPN 配置之外:
dev tun
port 1194
proto udp
mode server
tls-server
server 192.168.255.0 255.255.255.0
push "route 192.168.255.0 255.255.255.0"
route 192.168.0.0 255.255.255.0 192.168.255.2
push "dhcp-option DNS 192.168.255.1"
client-config-dir /etc/openvpn/ccd
client-to-client
ifconfig-pool-persist addr_list
comp-lzo
tun-mtu 1500
keepalive 10 60
persist-key
persist-tun
cipher DES-EDE3-CBC
ca /etc/openvpn/ca.crt
cert /etc/openvpn/server.crt
key /etc/openvpn/server.key
dh /etc/openvpn/dh1024.pem
tls-auth /etc/openvpn/ta.key 0
status openvpn-status.log
log /var/log/openvpn/openvpn.log
verb 4
FreeBSD 的配置:
client
proto udp
dev tun
remote xx.xx.xx.xx 1194
comp-lzo
resolv-retry infinite
persist-tun
persist-key
ca /usr/local/etc/openvpn/ca.crt
cert /usr/local/etc/openvpn/freebsd-client.crt
key /usr/local/etc/openvpn/freebsd-client.key
dh /usr/local/etc/openvpn/dh1024.pem
tls-auth /usr/local/etc/openvpn/ta.key 1
tls-client
cipher DES-EDE3-CBC # Triple-DES
verb 4
route-method exe
route-delay 2
ping 100
ping-restart 200
/etc/openvpn/ccd/freebsd-client内容:
push "route 192.168.255.0 255.255.255.0"
iroute 192.168.0.0 255.255.255.0
在 FreeBSD 上:
# ps aux | grep natd
/sbin/natd -n re0
/sbin/natd -n tun0 -p 8669
# ipfw show
00039 12203 876046 fwd 192.168.0.111,80 tcp from 192.168.0.0/24 to 192.168.0.111 dst-port 80
00040 322269 40046856 fwd 192.168.0.111,3128 tcp from 192.168.0.0/24 to any dst-port 80,433,8080
00050 2885463 1611968772 divert 8668 ip4 from any to any via re0
00060 5675 1094008 divert 8669 ip from any to any via tun0
00100 28440 2126360 allow ip from any to any via lo0
00200 0 0 deny ip from any to 127.0.0.0/8
00300 0 0 deny ip from 127.0.0.0/8 to any
65000 4241769 2426143908 allow ip from any to any
65535 1 78 deny ip from any to any
# netstat -nr -finet
Routing tables
Internet:
Destination Gateway Flags Refs Use Netif Expire
default 192.168.1.1 UGS 22 3312575 re0
127.0.0.1 link#4 UH 0 56564 lo0
192.168.0.0/24 link#1 U 3 166750211 bge0
192.168.0.111 link#1 UHS 0 12 lo0
192.168.1.0/24 link#2 U 1 235840 re0
192.168.1.2 link#2 UHS 0 36 lo0
192.168.255.0/24 192.168.255.5 UGS 0 20 tun0
192.168.255.5 link#5 UH 0 0 tun0
192.168.255.6 link#5 UHS 0 0 lo0
在 CentOS 上:
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.255.2 * 255.255.255.255 UH 0 0 0 tun0
xx.xx.xx.0 * 255.255.255.0 U 0 0 0 eth0
xx.xx.yy.0 * 255.255.255.0 U 0 0 0 eth0
192.168.0.0 192.168.255.2 255.255.255.0 UG 0 0 0 tun0
192.168.122.0 * 255.255.255.0 U 0 0 0 virbr0
192.168.255.0 192.168.255.2 255.255.255.0 UG 0 0 0 tun0
169.254.0.0 * 255.255.0.0 U 0 0 0 eth0
default xx.xx.xx.1 0.0.0.0 UG 0 0 0 eth0
$ ip route get 192.168.0.111
192.168.0.111 via 192.168.255.2 dev tun0 src 192.168.255.1
cache mtu 1500 advmss 1460 hoplimit 64
我从 CentOS ping 192.168.0.111 并得到以下结果:
在 CentOS 上:
$ tcpdump -i tun0
tcpdump: WARNING: arptype 65534 not supported by libpcap - falling back to cooked socket
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type LINUX_SLL (Linux cooked), capture size 96 bytes
11:34:48.963629 IP 192.168.255.1 > 192.168.0.111: ICMP echo request, id 40524, seq 1, length 64
11:34:49.973944 IP 192.168.255.1 > 192.168.0.111: ICMP echo request, id 40524, seq 2, length 64
11:34:50.974007 IP 192.168.255.1 > 192.168.0.111: ICMP echo request, id 40524, seq 3, length 64
11:34:51.974075 IP 192.168.255.1 > 192.168.0.111: ICMP echo request, id 40524, seq 4, length 64
关于 FreeBSD 的沉默:
tcpdump -i tun0
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type NULL (BSD loopback), capture size 96 bytes
有谁能够帮助我?
答案1
您确定接口之间的路由已激活吗?/proc/sys/net/ipv4/ip_forward
尝试离开 VPN 之前,请先尝试 ping VPN。
答案2
如果我是你,我会看看 ClearOS。它是一个基于 CentOS 的系统,具有出色的基于 Web 的 GUI,它可以在大约 15 分钟内完成您想要它做的事情。它不必是您的网关,并且根据您的问题判断,我相信您可以将其配置为您网络上的设备。它可以提供 PPTP 和 OpenVPN,以防您的 Windows 用户也需要访问。


