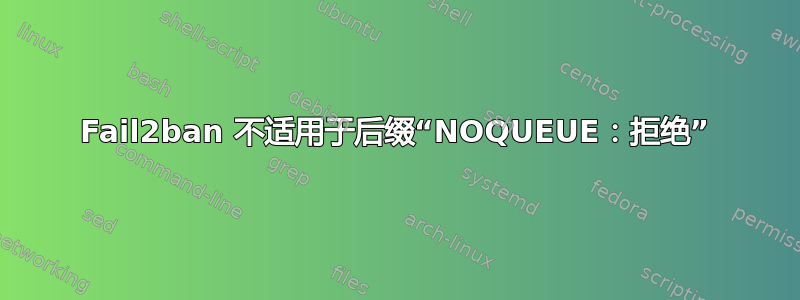
我的 postfix 实例 (Debian 9) 一直受到垃圾邮件发送者机器人的攻击,这些机器人试图将其用作开放中继。我已启动并运行 fai2ban,它可以完美抵御 SASL 攻击,但我无法让它抵御中继攻击。日志条目如下所示:
NOQUEUE: reject: RCPT from unknown[173.82.219.107]: 450 4.7.25 Client host rejected: cannot find your hostname, [173.82.219.107]; from=<[email protected]> to=<[email protected]> proto=ESMTP helo=<example.com>
我已使用以下命令为 postfix 激活 fai2ban:
[postfix]
enabled = true
port = smtp,465,submission
logpath = %(postfix_log)s
backend = %(postfix_backend)s
[postfix-rbl]
enabled = true
port = smtp,465,submission
logpath = %(postfix_log)s
backend = %(postfix_backend)s
maxretry = 1
[postfix-sasl]
enabled = true
port = smtp,465,submission,imap,imaps,pop3,pop3s
logpath = %(postfix_log)s
backend = %(postfix_backend)s
maxretry = 3
我根据 postfix 的错误信息似乎发生了变化的事实编辑了正则表达式。基本上我改成\.1了\.\d+:
[Definition]
_daemon = postfix(-\w+)?/(?:submission/|smtps/)?smtp[ds]
_port = (?::\d+)?
failregex = ^%(__prefix_line)sNOQUEUE: reject: RCPT from \S+\[<HOST>\]: 554 5\.7\.1 .*$
^%(__prefix_line)sNOQUEUE: reject: RCPT from \S+\[<HOST>\]: 450 4\.7\.\d+ Client host rejected: cannot find your hostname, (\[\S*\]); from=<\S*> to=<\S+> proto=ESMTP helo=<\S*>$
^%(__prefix_line)sNOQUEUE: reject: RCPT from \S+\[<HOST>\]: 450 4\.7\.\d+ : Helo command rejected: Host not found; from=<> to=<> proto=ESMTP helo= *$
^%(__prefix_line)sNOQUEUE: reject: EHLO from \S+\[<HOST>\]: 504 5\.5\.\d+ <\S+>: Helo command rejected: need fully-qualified hostname;
^%(__prefix_line)sNOQUEUE: reject: VRFY from \S+\[<HOST>\]: 550 5\.1\.1 .*$
^%(__prefix_line)sNOQUEUE: reject: RCPT from \S+\[<HOST>\]: 450 4\.1\.\d+ <\S*>: Sender address rejected: Domain not found; from=<\S*> to=<\S+> proto=ESMTP helo=<\S*>$
^%(__prefix_line)simproper command pipelining after \S+ from [^[]*\[<HOST>\]:?$
^%(__prefix_line)sNOQUEUE: reject: RCPT from (.*)\[<HOST>\]: 450 4\.7\.\d+ .*$
ignoreregex =
[Init]
journalmatch = _SYSTEMD_UNIT=postfix.service
# Author: Cyril Jaquier
但是 fail2ban 无法识别上述攻击。因此我使用了 fail2ban-regex to check if the above mentioned regular expressions do apply. I put the above cited line from the logfile twice in an custom filelogtest.log` 并执行了以下操作:
fail2ban-regex ~/logtest.log /etc/fail2ban/filter.d/postfix.conf
在我看来正则表达式确实起作用了,因为我得到:
Running tests
=============
Use failregex filter file : postfix, basedir: /etc/fail2ban
Use log file : /root/logtest.log
Use encoding : UTF-8
Results
=======
Failregex: 2 total
|- #) [# of hits] regular expression
| 2) [2] ^(?:\[\])?\s*(?:<[^.]+\.[^.]+>\s+)?(?:\S+\s+)?(?:kernel: \[ *\d+\.\d+\]\s+)?(?:@vserver_\S+\s+)?(?:(?:(?:\[\d+\])?:\s+[\[\(]?postfix(-\w+)?/(?:submission/|smtps/)?smtp[ds](?:\(\S+\))?[\]\)]?:?|[\[\(]?postfix(-\w+)?/(?:submission/|smtps/)?smtp[ds](?:\(\S+\))?[\]\)]?:?(?:\[\d+\])?:?)\s+)?(?:\[ID \d+ \S+\]\s+)?NOQUEUE: reject: RCPT from \S+\[<HOST>\]: 450 4\.7\.\d+ Client host rejected: cannot find your hostname, (\[\S*\]); from=<\S*> to=<\S+> proto=ESMTP helo=<\S*>$
`-
Ignoreregex: 0 total
Date template hits:
|- [# of hits] date format
| [2] (?:DAY )?MON Day 24hour:Minute:Second(?:\.Microseconds)?(?: Year)?
`-
Lines: 2 lines, 0 ignored, 2 matched, 0 missed
[processed in 0.00 sec]
但 fail2ban 仍然无法识别攻击。我做错了什么?
答案1
尝试更通用的配置来捕获更多。
以下是一个例子fail2ban 维基
failregex = reject: RCPT from (.*)\[<HOST>\]: 550 5.1.1
reject: RCPT from (.*)\[<HOST>\]: 450 4.7.1
reject: RCPT from (.*)\[<HOST>\]: 554 5.7.1


