我是一个非常快乐的 OpenVPN 用户,出于安全和性能的原因,我决定将所有东西切换到 Wireguard。
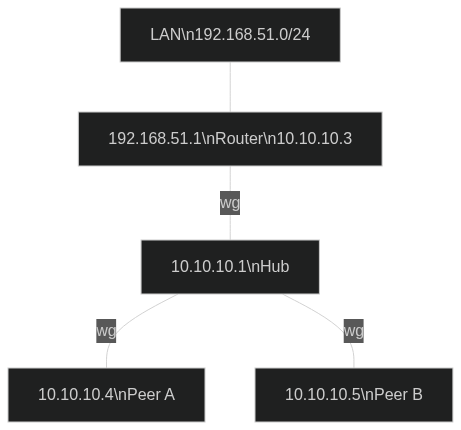
主要目标是能够从外部访问办公室专用局域网。办公室路由器和外部对等点都在防火墙后面,所以我决定采用 Hub and Spoke 配置。集线器位于具有公共 IP 的 Linux 云 VPS 上。配置与我目前使用 OpenVPN 时采用的配置相同:有一个可从互联网访问的服务器和几个连接到 VPN 时可以相互通信的客户端。其中一个是路由器,它将其专用局域网暴露给其他客户端。
我将办公室路由器用作带有 VPN Fusion 的 WG 客户端(它是 ASUS RT-AX92U),并且我能够看到 VPN 和私有 LAN 中的所有其他计算机。
VPN address range = 10.10.10.0/24
LAN address range = 192.168.51.0/24
router address LAN = 192.168.51.1
router address VPN = 10.10.10.3
wireguard hub = 10.10.10.1
peer A = 10.10.10.4
peer B = 10.10.10.5
主要问题是我无法从 VPN 直接连接到路由器。10.10.10.3 和 192.168.51.1 均无响应。此外,ping 也不起作用。我不知道这是由于防火墙还是 WG 配置造成的。使用 OpenVPN 一切正常。当然可以从私有 LAN 访问路由器。
我找到了类似的问题,但我已经尝试了建议的解决方案,但没有成功。有些事情我就是搞不懂……
请参阅以下集线器的配置文件:
[Interface]
Address = 10.10.10.1/32
ListenPort = 51820
PrivateKey = ************
PreUp = iptables -t mangle -A PREROUTING -i wg0 -j MARK --set-mark 0x30
PreUp = iptables -t nat -A POSTROUTING ! -o wg0 -m mark --mark 0x30 -j MASQUERADE
PostDown = iptables -t mangle -D PREROUTING -i wg0 -j MARK --set-mark 0x30
PostDown = iptables -t nat -D POSTROUTING ! -o wg0 -m mark --mark 0x30 -j MASQUERADE
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.3/32, 192.168.51.0/24
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.4/32
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.5/32
路由器的配置文件
[Interface]
Address = 10.10.10.3/32
PrivateKey = ********
[Peer]
PublicKey = ********
PresharedKey = ********
AllowedIPs = 10.10.10.0/24
Endpoint = cloudIP:51820
以及 Peer B 的配置文件(Peer A 相同)
[Interface]
Address = 10.10.10.5/32
PrivateKey = ********
[Peer]
PublicKey = ********
PresharedKey = ********
AllowedIPs = 10.10.10.0/24, 192.168.51.0/24
Endpoint = cloudIP:51820
编辑1
在对@Robbie 进行彻底分析后,我更加关注防火墙设置。确实,按照他建议的方式调整 hub wg0.conf 文件可以像以前一样工作,所以我删除了 MASQUERADE 行并添加了 ip-forward 行,在系统级别恢复 ip-forward = 0。
我在 Peer A 上运行了 traceroute 命令,同时激活了 hub 上的 tcpdump,得到了以下结果:
在对等点 A 上
C:\Users\inter> TRACERT.EXE 192.168.51.55
Tracing route to 192.168.51.55 over a maximum of 30 hops
1 23 ms 23 ms 23 ms 10.10.10.1
2 * * * Request timed out.
3 42 ms 40 ms 40 ms 192.168.51.55
Trace complete.
在中心
[root@remoto3 wireguard]# tcpdump -tttnei wg0
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on wg0, link-type RAW (Raw IP), capture size 262144 bytes
00:00:00.000000 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4540, length 72
00:00:00.000038 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4540, length 72
00:00:00.019062 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4540, length 72
00:00:00.000023 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4540, length 72
00:00:00.023966 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4541, length 72
00:00:00.000022 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4541, length 72
00:00:00.018760 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4541, length 72
00:00:00.000021 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4541, length 72
00:00:00.021823 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4542, length 72
00:00:00.000020 ip: 10.10.10.4 > 192.168.51.55: ICMP echo request, id 1, seq 4542, length 72
00:00:00.018592 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4542, length 72
00:00:00.000021 ip: 192.168.51.55 > 10.10.10.4: ICMP echo reply, id 1, seq 4542, length 72
00:00:00.442107 ip: 10.10.10.4.netbios-ns > 192.168.51.55.netbios-ns: UDP, length 50
00:00:00.000135 ip: 10.10.10.1 > 10.10.10.4: ICMP host 192.168.51.55 unreachable - admin prohibited filter, length 86
00:00:01.503801 ip: 10.10.10.4.netbios-ns > 192.168.51.55.netbios-ns: UDP, length 50
00:00:00.000089 ip: 10.10.10.1 > 10.10.10.4: ICMP host 192.168.51.55 unreachable - admin prohibited filter, length 86
00:00:01.515731 ip: 10.10.10.4.netbios-ns > 192.168.51.55.netbios-ns: UDP, length 50
00:00:00.000121 ip: 10.10.10.1 > 10.10.10.4: ICMP host 192.168.51.55 unreachable - admin prohibited filter, length 86
00:10:07.780807 ip: 10.10.10.4 > 192.168.51.1: ICMP echo request, id 1, seq 4543, length 40
00:00:00.000106 ip: 10.10.10.4 > 192.168.51.1: ICMP echo request, id 1, seq 4543, length 40
00:00:04.668951 ip: 10.10.10.4 > 192.168.51.1: ICMP echo request, id 1, seq 4544, length 40
00:00:00.000044 ip: 10.10.10.4 > 192.168.51.1: ICMP echo request, id 1, seq 4544, length 40
00:00:42.525787 ip: 10.10.10.4 > 10.10.10.1: ICMP echo request, id 1, seq 4545, length 40
00:00:00.000148 ip: 10.10.10.1 > 10.10.10.4: ICMP echo reply, id 1, seq 4545, length 40
00:00:01.019225 ip: 10.10.10.4 > 10.10.10.1: ICMP echo request, id 1, seq 4546, length 40
00:00:00.000073 ip: 10.10.10.1 > 10.10.10.4: ICMP echo reply, id 1, seq 4546, length 40
00:00:14.268544 ip: 10.10.10.4 > 10.10.10.3: ICMP echo request, id 1, seq 4547, length 40
00:00:00.000170 ip: 10.10.10.4 > 10.10.10.3: ICMP echo request, id 1, seq 4547, length 40
00:00:04.684129 ip: 10.10.10.4 > 10.10.10.3: ICMP echo request, id 1, seq 4548, length 40
00:00:00.000040 ip: 10.10.10.4 > 10.10.10.3: ICMP echo request, id 1, seq 4548, length 40
似乎实际上有某种东西正在过滤流量,我怀疑它是路由器防火墙,尽管它的 IP 地址没有清楚地出现在此输出中,但我已经尝试放松它但没有成功......
編輯2
我按照@Robbie 在评论中建议的方式,从 WG 网络上的一位同行那里运行测试,正如预期的那样,路由器过滤了所有内容。
[root@peer ~]$ nmap -Pn 10.10.10.3
Starting Nmap 7.92 ( https://nmap.org ) at 2023-12-11 09:00 CET
Nmap scan report for 10.10.10.3
Host is up.
All 1000 scanned ports on 10.10.10.3 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 201.47 seconds
这肯定是与路由器防火墙有关的问题,Wireguard 设置是正确的。我会处理这个问题。
答案1
首先,这是我对您的设置的理解。
我使用网络命名空间来构建您的网络玩具模型并部署您的配置(不幸的是,我没有时间按比例构建它或绘制它)
#!/bin/bash
sudo true
sudo ./newHub.sh wan
sudo ./newHub.sh lan
sudo ./newHost.sh router
sudo ./newHost.sh lanA
sudo ./newHost.sh lanB
sudo ./hostToHub.sh router eth0 192.168.51.1/24 lan
sudo ./hostToHub.sh lanA eth0 192.168.51.101/24 lan
sudo ./hostToHub.sh lanB eth0 192.168.51.102/24 lan
sudo ip netns exec router sysctl net.ipv4.ip_forward=1
sudo ip -n lanA route add default via 192.168.51.1
sudo ip -n lanB route add default via 192.168.51.1
sudo ./newHost.sh hub
sudo ./newHost.sh peerA
sudo ./newHost.sh peerB
sudo ./hostToHub.sh router wan0 172.16.0.1/24 wan
sudo ./hostToHub.sh hub wan0 172.16.0.2/24 wan
sudo ./hostToHub.sh peerA wan0 172.16.0.3/24 wan
sudo ./hostToHub.sh peerB wan0 172.16.0.4/24 wan
sudo ip netns exec router wg-quick up ./wg/router/wg0.conf # 10.10.10.3
sudo ip netns exec hub wg-quick up ./wg/hub/wg0.conf # 10.10.10.1
sudo ip netns exec peerA wg-quick up ./wg/peerA/wg0.conf # 10.10.10.4
sudo ip netns exec peerB wg-quick up ./wg/peerB/wg0.conf # 10.10.10.5
每个都wg0.conf与您的示例相匹配。在此阶段,每个 wireguard 对等点都可以 ping 中心集线器,但不能互相 ping。我实际上并不认为您的伪装规则实际上在做任何事情,所以我删除了它们,并将它们添加sysctl net.ipv4.ip_forward=1到集线器的 wg0.conf 中。
摘自 wg/hub/wg.conf
PreUp = sysctl net.ipv4.ip_forward=1
PostDown = sysctl net.ipv4.ip_forward=0
然后一切都顺利进行。
[root@orobas virtopology]# traceroute 192.168.51.101 # ping to a device on the router's lan, from peerA
traceroute to 192.168.51.101 (192.168.51.101), 30 hops max, 60 byte packets
1 10.10.10.1 (10.10.10.1) 0.541 ms 0.531 ms 0.523 ms
2 10.10.10.3 (10.10.10.3) 0.969 ms 0.966 ms 1.039 ms
3 192.168.51.101 (192.168.51.101) 1.041 ms 1.044 ms 1.037 ms
[root@orobas virtopology]#
希望这可以帮助