我正在处理 PCI-DSS 扫描器报告的漏洞,其中一个漏洞对我来说是新的:
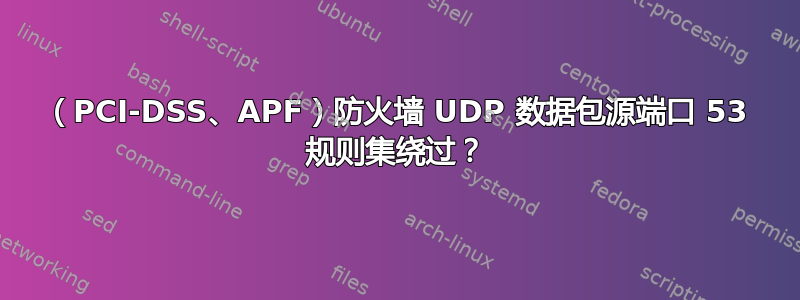
标题
防火墙 UDP 数据包源端口 53 规则集绕过
概要:
防火墙规则集可以被绕过。
影响:
通过发送源端口为 53 的 UDP 数据包,可以绕过远程防火墙的规则。攻击者可以利用此漏洞向远程主机注入 UDP 数据包,而无需担心防火墙的存在。
也可以看看 :
http://archives.neohapsis.com/archives/fulldisclosure/2003-q2/0352.html
http://www.nessus.org/u?4368bb37
第一篇链接文章给出了一个漏洞利用证明命令,nmap -v -P0 -sU -p 1900 ${IP} -g 53如果源端口为 53,该命令确实会返回一个 56 字节的数据包。但为什么呢?在这个例子中,它报告端口 1900 已“关闭”,但返回了一个 56 字节的回复。相比之下,对端口 1900 的请求(UDP 源端口 123(也打开))返回 0 字节。
#
# Source port 53:
#
$ sudo nmap -v -P0 -sU -p 1900 ${IP} -g 53
Starting Nmap 6.47 ( http://nmap.org ) at 2015-11-24 20:19 CST
Initiating Parallel DNS resolution of 1 host. at 20:19
Completed Parallel DNS resolution of 1 host. at 20:19, 0.00s elapsed
Initiating UDP Scan at 20:19
Scanning *HOST* (*IP*) [1 port]
Completed UDP Scan at 20:19, 0.21s elapsed (1 total ports)
Nmap scan report for *HOST* (*IP*)
Host is up (0.038s latency).
PORT STATE SERVICE
1900/udp closed upnp
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.25 seconds
Raw packets sent: 1 (28B) | Rcvd: 1 (56B)
#
# Source Port 123:
#
$ sudo nmap -v -P0 -sU -p 1900 ${IP} -g 123
Starting Nmap 6.47 ( http://nmap.org ) at 2015-11-24 20:20 CST
Initiating Parallel DNS resolution of 1 host. at 20:20
Completed Parallel DNS resolution of 1 host. at 20:20, 0.00s elapsed
Initiating UDP Scan at 20:20
Scanning *HOST* (*IP*) [1 port]
Completed UDP Scan at 20:20, 2.42s elapsed (1 total ports)
Nmap scan report for *HOST* (*IP*)
Host is up.
PORT STATE SERVICE
1900/udp open|filtered upnp
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2.46 seconds
Raw packets sent: 2 (56B) | Rcvd: 0 (0B)
该 Linux 服务器正在运行控制面板 (InterWorx-CP),该控制面板管理 APF 安装,进而生成 iptables 规则。它们如下:
$ sudo iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere
REFRESH_TEMP all -- anywhere anywhere
TALLOW all -- anywhere anywhere
TGALLOW all -- anywhere anywhere
TDENY all -- anywhere anywhere
TGDENY all -- anywhere anywhere
DROP tcp -- anywhere anywhere tcp dpts:epmap:netbios-ssn
DROP udp -- anywhere anywhere udp dpts:epmap:netbios-ssn
DROP tcp -- anywhere anywhere tcp dpt:sunrpc
DROP udp -- anywhere anywhere udp dpt:sunrpc
DROP tcp -- anywhere anywhere tcp dpt:login
DROP udp -- anywhere anywhere udp dpt:who
DROP tcp -- anywhere anywhere tcp dpt:microsoft-ds
DROP udp -- anywhere anywhere udp dpt:microsoft-ds
DROP tcp -- anywhere anywhere tcp dpt:ms-sql-s
DROP udp -- anywhere anywhere udp dpt:ms-sql-s
DROP tcp -- anywhere anywhere tcp dpt:ms-sql-m
DROP udp -- anywhere anywhere udp dpt:ms-sql-m
DROP tcp -- anywhere anywhere tcp dpt:search-agent
DROP udp -- anywhere anywhere udp dpt:search-agent
DROP tcp -- anywhere anywhere tcp dpt:ingreslock
DROP udp -- anywhere anywhere udp dpt:ingreslock
DROP tcp -- anywhere anywhere tcp dpt:ctx-bridge
DROP udp -- anywhere anywhere udp dpt:ctx-bridge
ACCEPT tcp -- anywhere anywhere tcp dpt:ftp
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:lmtp
ACCEPT tcp -- anywhere anywhere tcp dpt:smtp
ACCEPT tcp -- anywhere anywhere tcp dpt:http
ACCEPT tcp -- anywhere anywhere tcp dpt:pop3
ACCEPT tcp -- anywhere anywhere tcp dpt:imap
ACCEPT tcp -- anywhere anywhere tcp dpt:https
ACCEPT tcp -- anywhere anywhere tcp dpt:imaps
ACCEPT tcp -- anywhere anywhere tcp dpt:pop3s
ACCEPT tcp -- anywhere anywhere tcp dpt:autodesk-nlm
ACCEPT tcp -- anywhere anywhere tcp dpt:powerclientcsf
ACCEPT tcp -- anywhere anywhere tcp dpts:50000:51000
ACCEPT tcp -- anywhere anywhere tcp dpt:submission
ACCEPT udp -- anywhere anywhere udp dpt:ftp-data
ACCEPT udp -- anywhere anywhere udp dpt:ftp
ACCEPT udp -- anywhere anywhere udp dpt:ntp
ACCEPT udp -- anywhere anywhere udp dpt:domain
ACCEPT icmp -- anywhere anywhere icmp destination-unreachable limit: avg 14/sec burst 5
ACCEPT icmp -- anywhere anywhere icmp redirect limit: avg 14/sec burst 5
ACCEPT icmp -- anywhere anywhere icmp time-exceeded limit: avg 14/sec burst 5
ACCEPT icmp -- anywhere anywhere icmp echo-reply limit: avg 14/sec burst 5
ACCEPT icmp -- anywhere anywhere icmp type 30 limit: avg 14/sec burst 5
ACCEPT icmp -- anywhere anywhere icmp echo-request limit: avg 14/sec burst 5
DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN state NEW
ACCEPT tcp -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT udp -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT udp -- anywhere anywhere udp spt:domain dpts:1023:65535
ACCEPT tcp -- anywhere anywhere tcp spt:domain dpts:1023:65535
DROP tcp -- anywhere anywhere
DROP udp -- anywhere anywhere
DROP all -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN TCPMSS clamp to PMTU
REFRESH_TEMP all -- anywhere anywhere
TALLOW all -- anywhere anywhere
TGALLOW all -- anywhere anywhere
TDENY all -- anywhere anywhere
TGDENY all -- anywhere anywhere
DROP tcp -- anywhere anywhere tcp dpts:epmap:netbios-ssn
DROP udp -- anywhere anywhere udp dpts:epmap:netbios-ssn
DROP tcp -- anywhere anywhere tcp dpt:sunrpc
DROP udp -- anywhere anywhere udp dpt:sunrpc
DROP tcp -- anywhere anywhere tcp dpt:login
DROP udp -- anywhere anywhere udp dpt:who
DROP tcp -- anywhere anywhere tcp dpt:microsoft-ds
DROP udp -- anywhere anywhere udp dpt:microsoft-ds
DROP tcp -- anywhere anywhere tcp dpt:ms-sql-s
DROP udp -- anywhere anywhere udp dpt:ms-sql-s
DROP tcp -- anywhere anywhere tcp dpt:ms-sql-m
DROP udp -- anywhere anywhere udp dpt:ms-sql-m
DROP tcp -- anywhere anywhere tcp dpt:search-agent
DROP udp -- anywhere anywhere udp dpt:search-agent
DROP tcp -- anywhere anywhere tcp dpt:ingreslock
DROP udp -- anywhere anywhere udp dpt:ingreslock
DROP tcp -- anywhere anywhere tcp dpt:ctx-bridge
DROP udp -- anywhere anywhere udp dpt:ctx-bridge
ACCEPT tcp -- anywhere anywhere tcp dpts:1024:65535 state RELATED,ESTABLISHED
ACCEPT udp -- anywhere anywhere udp dpts:1024:65535 state RELATED,ESTABLISHED
ACCEPT udp -- anywhere anywhere udp spts:1023:65535 dpt:domain
ACCEPT tcp -- anywhere anywhere tcp spts:1023:65535 dpt:domain
ACCEPT all -- anywhere anywhere
Chain PROHIBIT (0 references)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain REFRESH_TEMP (2 references)
target prot opt source destination
Chain RESET (0 references)
target prot opt source destination
REJECT tcp -- anywhere anywhere reject-with tcp-reset
Chain TALLOW (2 references)
target prot opt source destination
Chain TDENY (2 references)
target prot opt source destination
Chain TGALLOW (2 references)
target prot opt source destination
Chain TGDENY (2 references)
target prot opt source destination
该服务器也是其托管域的 DNS 授权机构,可复制到从属服务器,因此可以禁用传入的 DNS 查询。但即使我在 CP 中执行此操作,漏洞利用仍然成功。我猜 APF 正在生成一些不受我间接控制的规则。
我该如何堵住防火墙上的这个漏洞呢?
这个 2003 年出现的漏洞有何影响?PCI 扫描器现在才报告该漏洞(已进行多年扫描)?
答案1
他们使用端口 53 进行测试,因为它很可能是开放的(即 DNS 使用的端口)。
我遇到了同样的错误,解决方法是编写两条规则。
首先,您现在可以为 UDP 设置 ESTABLISHED 和 RELATED 规则。这在以前是不可能的,因为 UDP 被认为是无状态的,但他们通过跟踪发送的内容和接受的内容添加了该功能有关的回复。
-A INPUT -i eth0 -p udp -m state --state ESTABLISH,RELATED -m udp -d 1.2.3.4 -j ACCEPT
注意:使用正确的名称/IP 进行eth0更改1.2.3.4
然后,您可以为 DNS 服务器传入数据包打开端口 53。
-A INPUT -i eth0 -p udp -m udp --dport 53 -d 1.2.3.4 -j ACCEPT
注意:使用正确的名称/IP 进行eth0更改1.2.3.4
您现有的规则如下所示:
ACCEPT udp -- anywhere anywhere udp dpt:domain
它不受接口或目标地址的限制。它应该确保您不会从虚假来源获取数据。(例如,在 DigitalOcean 和可能许多其他网站上,有一个隐藏的 IP 地址……您不想接受来自该地址的数据;此外,我曾经出现过一次变形,接口名称也发生了变化!!!如果您有一个单一的网络连接,它应该很简单,但如果您无法控制硬件,您就无法知道什么时候会发生这种情况……)
话虽如此,规则集中最大的问题在于 INPUT 链中的第一行。它看起来像这样:
ACCEPT all -- anywhere anywhere
这意味着完全接受一切。之后的所有规则都将被忽略。换句话说,你根本没有防火墙……
您的 OUTPUT 链中有相同的第一条规则,我想这是为了确保您的防火墙不会阻止任何东西。
一句建议,写一个小脚本使用选项查看防火墙-nvx。-n通过不尝试转换 IP 地址,可以加快速度。-v显示每个规则上传输的数据包和字节数(即,如果规则接受数据包,则其数据包计数器将增加 1。)显示-x每个计数器的确切数字(而不是使其“人性化”),这样我就可以知道计数器何时增加了 1 或更多。这在测试时很重要。
如果您使用过,-nvx您可能会注意到,只有第一条规则的计数器针对 INPUT 和 OUTPUT 进行了递增。然后,您可能会疑惑为什么您从未在其他规则上获得命中...


