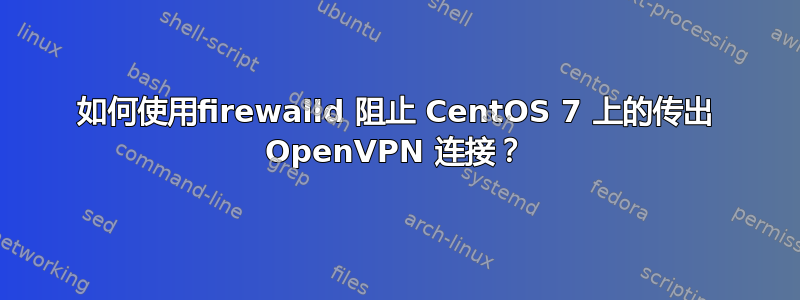
有:
192.168.1.0/24 网络(网关 192.168.1.1),可访问互联网(IP:345.45.67.89)
OpenVPN 服务器(CentOS 7)通过
eth0(192.168.1.2)连接(OpenVPN 端口:1194 |tun010.8.0.0/24 网络)网关 192.168.1.1 处的转发规则从 345.45.67.89:54321 到 192.168.1.2:1194
需要阻止 192.168.1.5 被 OpenVPN 客户端访问。
我正在尝试添加规则:
sudo firewall-cmd --direct --permanent --add-rule ipv4 filter OUTPUT 0 -d 192.168.1.5 -j DROP
通过服务器上的 ssh 访问curl http://192.168.1.5 -o out是 0%。但通过 OpenVPN 我可以访问http://192.168.1.5。
tun0启用了伪装,处于信任状态。看起来有问题。
我应该使用什么规则来从 10.8.0.0/24 删除到 192.168.1.5 的传出连接?
是否配置
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.2 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 XXX prefixlen 64 scopeid 0x20<link>
ether XXX txqueuelen 1000 (Ethernet)
RX packets 1176345 bytes 119424262 (113.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 23934 bytes 17136251 (16.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 344 (344.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 344 (344.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.8.0.1 netmask 255.255.255.255 destination 10.8.0.2
inet6 XXX prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 11947 bytes 904082 (882.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 15492 bytes 15376868 (14.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
sudo 防火墙cmd --list-all-zones
block
target: %%REJECT%%
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
dmz
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
drop
target: DROP
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
external
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
home
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
internal
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: openvpn ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
trusted (active)
target: ACCEPT
icmp-block-inversion: no
interfaces: tun0
sources:
services:
ports:
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
work
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
sudo 防火墙cmd --direct --get-all-rules
ipv4 filter OUTPUT 0 -d 192.168.1.5 -j DROP


